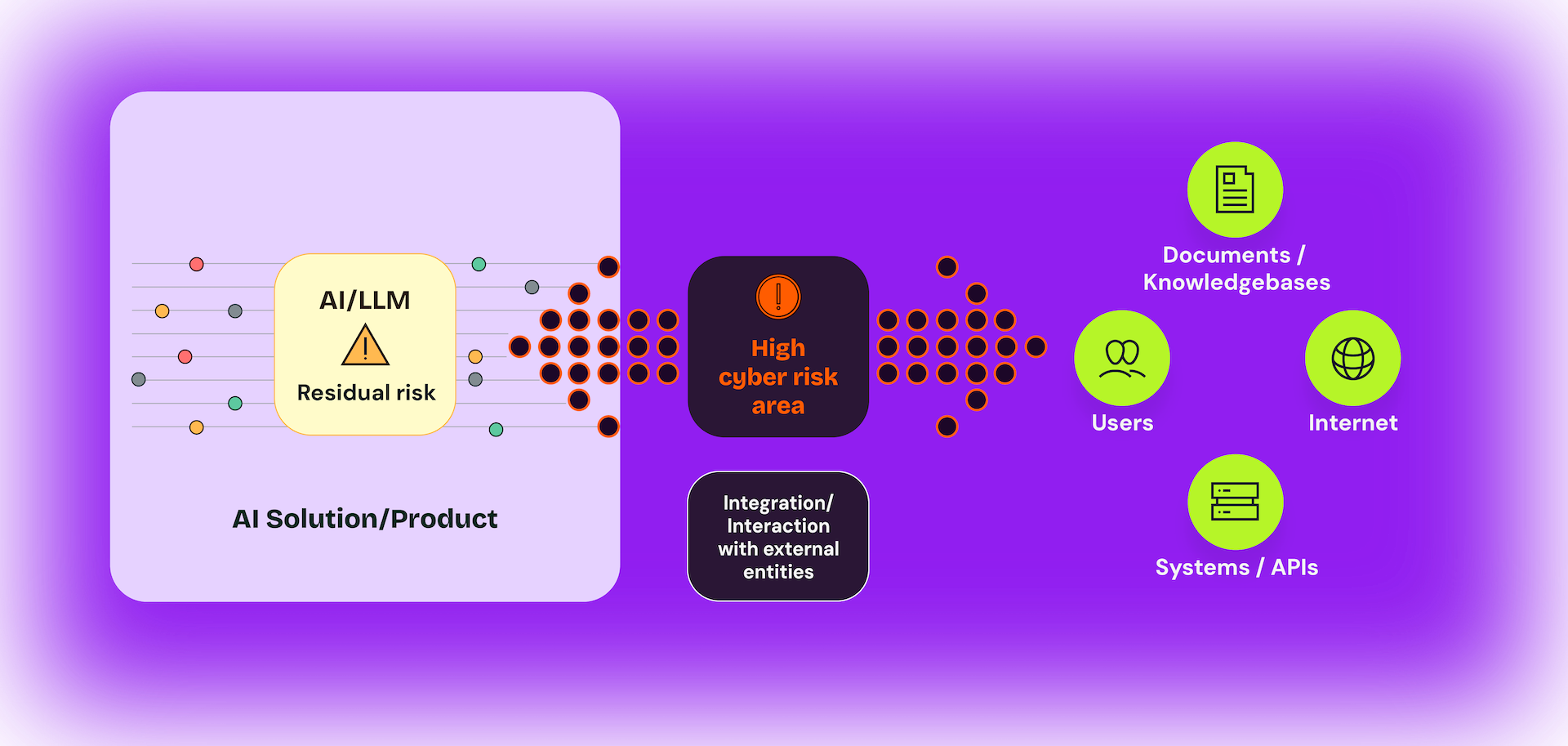
Common pitfalls in the use of GenAI
Practical risks associated with GenAI don’t exist in isolation but are mostly related to the context in which the organization is using it. When building GenAI and LLM integrations, it’s crucial to consider the potential security risks and implement robust safeguards from the outset.
These are the most common security pitfalls that we have identified associated with the use of AI for businesses.
Jailbreak and prompt injection attacks
Malicious actors attempt to “jailbreak” an LLM by injecting carefully crafted prompts, tricking it into executing unauthorized actions or revealing sensitive information.
Excessive agency and
malicious intent
GenAI systems with excessive agency get manipulated by attackers (via jailbreak and prompt injection attacks) causing the system to execute malicious actions and posing significant security risks.
Insecure tool/
plugin design
When tools, plugins, or integrations for LLMs are poorly designed or insecurely implemented, they can introduce significant vulnerabilities leading to unauthorized access and data breaches.
Insufficient monitoring, logging, and rate limiting
Inadequate monitoring, logging, and rate-limiting mechanisms hinder the detection of malicious activity, making it challenging to identify and respond to security incidents promptly.
Lack of
output validation
Failure to validate and sanitize the output from GenAI models can lead to the disclosure of confidential information or the introduction of client-side vulnerabilities like Cross-Site Scripting (XSS).
Ensure the security of your LLMs and GenAI solutions
Whether your organization is in the early stages of planning or developing GenAI-powered solutions, or already deploying these integrations or custom solutions, our consultants can help you identify and address potential cyber risks every step of the way.
We can support your organization in adopting and integrating AI securely by assessing the potential security flaws of the GenAI/ LLM integrations and interaction to your systems and workflows and providing recommendations on secure deployment.
Depending on your use case, the different assessment approaches may include any of the below.
Contact us to discuss the best approach for your specific case!
Governance, risk and threat modeling for AI
Our services to support you in the planning phase.
AI Governance
Defining the AI adoption objectives and acceptable use cases.
Adapting or creating ad-hoc risk management frameworks based on your organization’s needs and regulatory requirements.
AI Risk Modeling
Identifying and prioritizing security risks at an organizational and use case level.
Creating a shared risk understanding between development teams, cybersecurity, and business units.
AI Threat Modeling
Identifying the most relevant attack paths based on risk prioritization technical analysis.
Identifying control gaps and prioritizing control implementations through cost/ benefit analysis.
Implementation and integration of AI solutions
Our services to support you in the implementation phase.
Pentesting LLM Applications
Identifying and addressing the cybersecurity weaknesses in your organization’s LLM applications and integrations.
Understanding the exploit vulnerabilities of the LLM applications, the specific cyber risks they pose, and the attacker goals that will most likely lead to them being targeted.
Pentesting AI-supporting Infrastructure
Identifying high risk attack paths leading to your AI-powered applications and offering recommendations to protect these.
Ensuring secure hosting and AI-management, protecting AI data and access points.

Don’t be a stranger, let’s get in touch.
Our team of dedicated experts can help guide you in finding the right
solution for your unique issues. Complete the form and we are happy to
reach out as soon as possible to discuss more.
This site is protected by reCAPTCHA and the Google
Privacy Policy and Terms of Service apply.